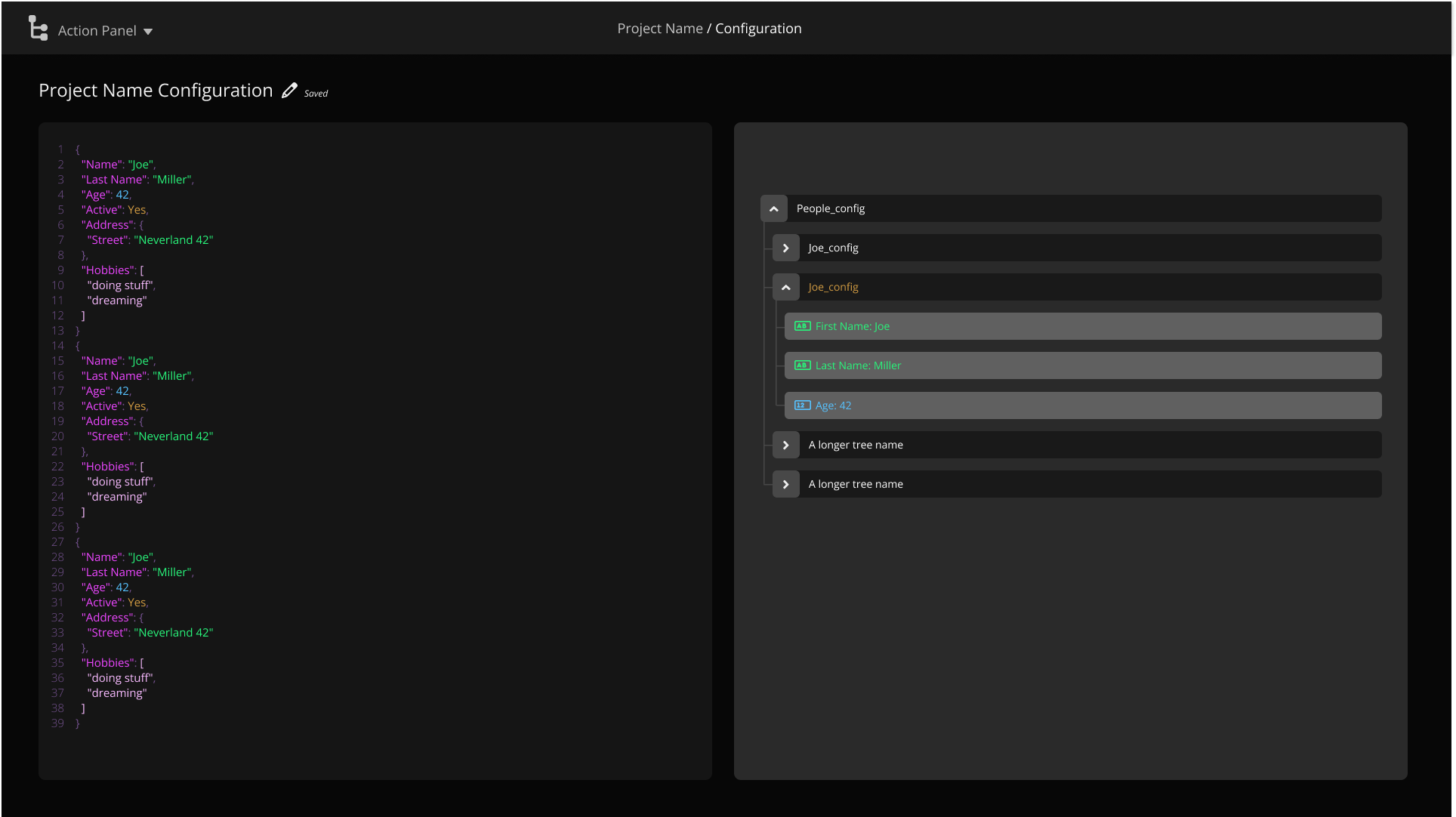
Methodology
RiskyTrees uses a researched-backed approach to risk analysis
Attack trees let you break down the complex
Attack trees provide a visual representation of potential threats and attack paths, making it easier for security professionals and stakeholders to understand complex scenarios. This visualization helps in communicating security risks effectively.
A systematic approach to analysis
The structured nature of attack trees allows for a systematic and organized analysis of potential vulnerabilities and attack vectors. This helps security teams to methodically identify and prioritize risks.
Risk Prioritization and Mitigation Planning
Identify where you are most at risk and develop mitigation strategies by breaking down potential attacks into specific steps and methods. This enables security professionals to design and implement countermeasures to address each identified risk.
Adaptive and dynamic
Attack trees are not static documents. With configurations, you can stress-test every decision you make. This adaptability ensures that security measures remain relevant and effective over time.