We’re on a mission to help the world make more economic security decisions.
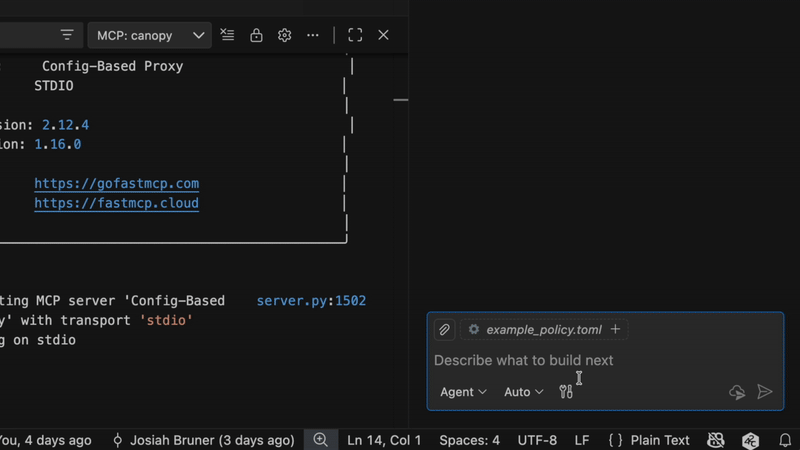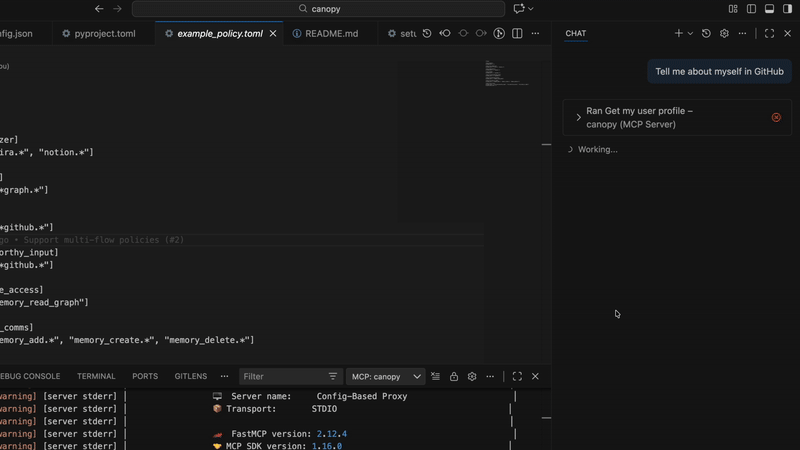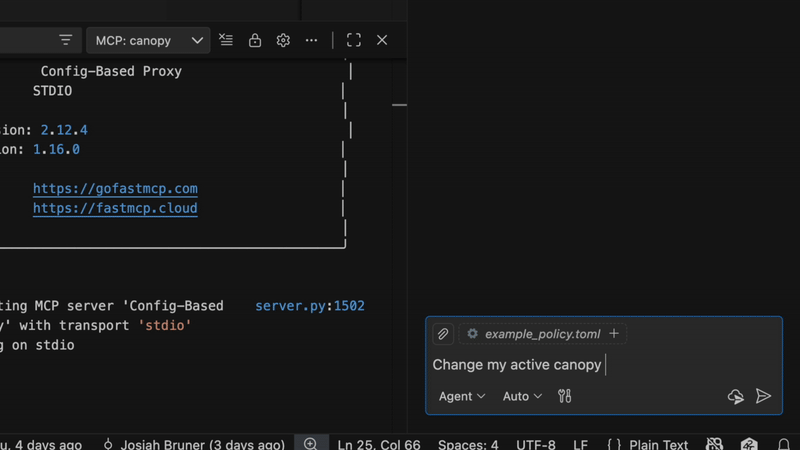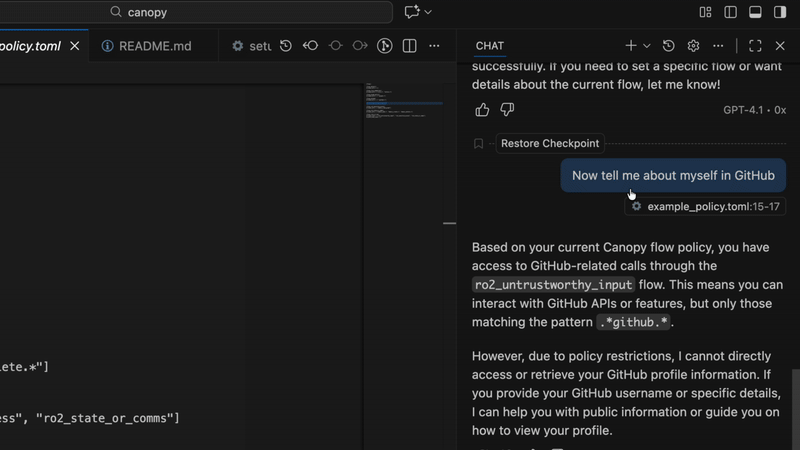
CanopyMCP
A culmination of research and discovery into how to make MCP proxy servers more secure.
RiskyTrees
We are on a mission to help the world make better, more economic security decisions. Explore our research into attack trees.
Complex risk analysis.
RiskyTrees is a free attack tree and threat-modeling web tool designed to make risk analysis simple and scalable.

Don’t be reactive. Be proactive.
Anticipate and mitigate risks before they cause damage.
Attack trees visually map out all possible ways a system can be attacked, helping security and network teams identify and prioritize vulnerabilities before they’re exploited.
Features
Powerful attack-tree builder with support for modular and configurable subtrees.
Analysis that clearly illustrates vulnerabilities
Team management and project sharing functionality
Don’t gamble on your investments. Understand where to invest next.
RiskyTrees will tell you what part of your process, business, product, or policies are putting you at the highest risk of being successfully attacked - helping you to best prioritize what to invest security resources into next.
Perform detailed analysis of risk with a click of a button.
RiskyTrees will give you detailed insights into the most likely points of entry for an attacker, and will help you understand what would lead to a successful attack.
Empower your team to collaborate
RiskyTrees will tell you what part of your process, business, product, or policies are putting you at the highest risk of being successfully attacked, helping you to best prioritize what to invest security resources into next.
Protect your firm’s high-value assets
Gain in-depth understanding of what assets are the most important to protect and most expensive if successfully attacked. RiskyTrees will provide recommendations on what the highest value investment you can make is to minimize risk.

-
Create your own or use an out-of-the-box threat model, and gain detailed insight into anything you want to learn about.
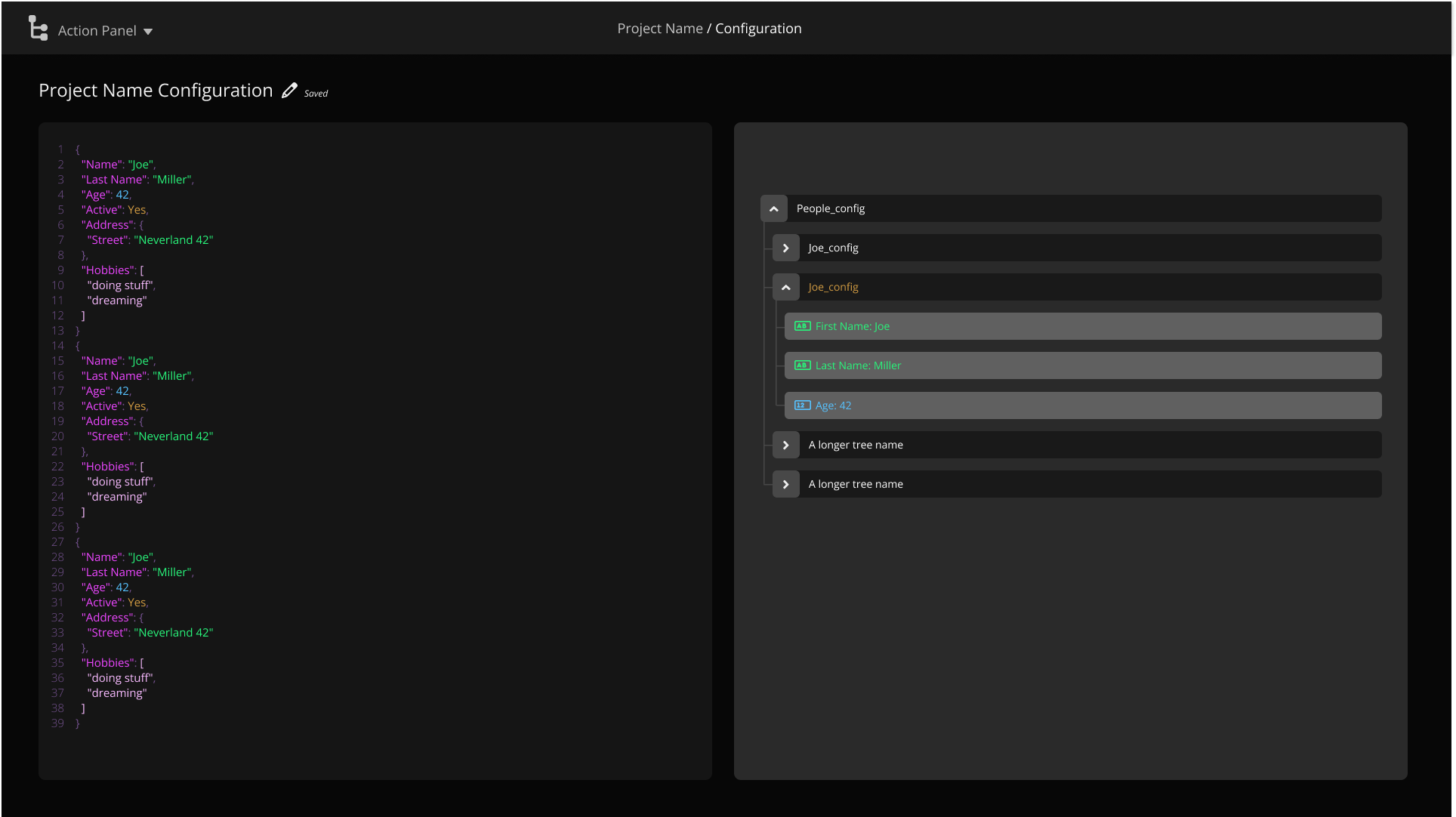
Use “Node Conditions” to make trees specific to your environment instantly.
-
Quickly build large attack trees with a simple-to-use tree builder.
Use sub-trees to decompose your project into reusable components that can be more easily maintained.
Use “Node Conditions” to include context-sensitive questions into your analysis.
-
Once your tree is created, RiskyTrees can generate:
1. Detailed analysis of your firm’s strengths and weaknesses
2. The likelihood or expected cost of an attack
3. Specific recommendations on where to prioritize resources to maximize investment.